UMS and Port Cybersecurity

KEY JUDGMENTS
▶︎ Increasing automation of port security operations will enlarge port attack surfaces and provide malicious actors with an expanding range of exploitable attack vectors.
▶︎ Port unmanned maritime systems (UMS) will be vulnerable to cyberattacks both as targets and as operational attack vectors.
▶︎ Adversary-manufactured UMS used in friendly foreign ports for surveillance and security operations could be used as platforms for adversary intelligence gathering or cyberattacks.
▶︎ Malicious actors could employ consumer/hobbyist UMS to infiltrate ports and coastal installations for purposes of covert intelligence gathering and cyber operations.
▶︎ UMS and underwater sensor networks present a unique cybersecurity vulnerability given their remote control or autonomous operations, increasing reliance on algorithmic processing and artificial intelligence, and eventual use of acoustic communication
In the nearly two decades since 9/11, the phrase "port security" has generally referred to safeguarding physical port infrastructure against kinetic attacks. But in the wake of several high profile maritime cyber attacks, such as Shahid Rajaee, and NotPetya, as well as the ongoing trend toward greater integration of information technology (IT) and operational technology (OT), the maritime sector has been thrust to the forefront of the national and global cybersecurity dialog.
Much of the available research on port cybersecurity focuses on threats and vulnerabilities originating within, or posed by, commercial operations - i.e. the web of interconnected IT and OT involved in navigation, communications, and the intermodal movement of cargo. But ports are also increasingly automating their physical security operations, from closed-circuit surface surveillance, to underwater intrusion detection systems (IDS), to unmanned maritime systems (UMS), the compromise of which could provide an attacker with access to port commercial information technology (IT) and operational technology (OT), as well as enable kinetic attacks on port infrastructure resulting in significant economic disruption and geopolitical instability. It is therefore imperative to understand the integrated nature of port cybersecurity threats and vulnerabilities arising from both commercial operations and physical port security.
What follows is an overview of potential port cybersecurity threats and vulnerabilities posed by UMS - underwater sensor networks, COTS and consumer/hobbyist unmanned surface vehicles (USVs), and COTS and consumer/hobbyist unmanned underwater vehicles (UUVs) - as well as cyberattack methods and scenarios involving UMS as either the victim or operational vector.
Abbreviations and Definitions:
AI - Artificial Intelligence
C2 - Command & Control
ISR - Intelligence, Surveillance, and Reconnaissance
USV - Unmanned Surface Vehicle
A remotely piloted or autonomous surface vehicle.UUV - Unmanned Underwater Vehicle
An umbrella term referring to AUVs and ROVs.AUV - Autonomous Underwater Vehicle
An untethered UUV that is capable of carrying out missions with little or no human intervention.ROV - Remotely Operated Vehicle
A UUV that utlizes an umbilical tether during operation.UMS - Unmanned Maritime Systems
An umbrella term referring to USVs and UUVs.UAS - Unmanned Aircraft System
An umbrella term referring to remotely piloted or autonomous air vehicles.IT - Information Technology
Computers, hardware, and software used in the management and manipulation of digital data.OT - Operational Technology
Hardware and software used to control devices and processes that interact with the physical world.COTS - "Commercial Off the Shelf" refers to platforms and technologies that can be purchased directly from manufacturers, specialty vendors, or online retailers, and serve a range of potential users from professional (science, industry, defense) to recreational.
Consumer/Hobbyist - Refers to a subset of COTS platforms and technologies that are user-friendly, low-cost, and generally appeal to recreational users only.
Active Intrusion - A cyberattack that involves the injection of malicious software to disrupt, degrade, damage, or gain control the victim's IT or OT.
Passive Intrusion - A cyberattack that involves intercepting or eavesdropping on victim communications or data transmissions.
UNDERWATER SENSOR NETWORKS
Advancements in acoustic and signal processing technologies have enabled the development of sophisticated underwater sensor networks to safeguard ports, coastal facilities, and offshore infrastructure against unauthorized underwater access.
-
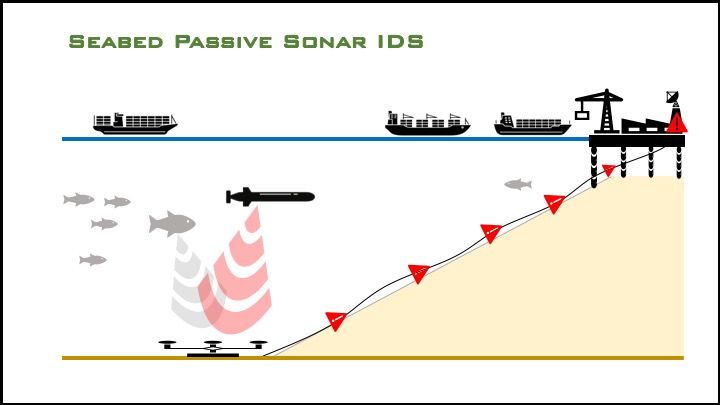
Underwater intrusion detection systems (IDS) provide a high rate of detection with a low incidence of false alarms. Though sometimes referred to as Diver Detection Systems/Sonar (DDS), these systems are capable of detecting and tracking a range of potential intruders, including closed-circuit (rebreather) divers, open circuit divers, UUVs, surface vehicles, and swimmer delivery vehicles.
-
IDS can be installed on the seabed, deployed over the side of moored or pierside vessels, or deployed through the hull of harbor patrol vessels.
-
IDS utilize active or passive sonar to detect, localize, and, using advanced algorithms, filter out noise disturbances to classify surface and/or underwater intruders. Research from MIT, Draper, and Woods Hole suggests that even micro-UUVs (six inches or less in diameter) could be passively detected in a cluttered, noisy port environment by isolating the sound of the brushless motors typically used in UUVs.
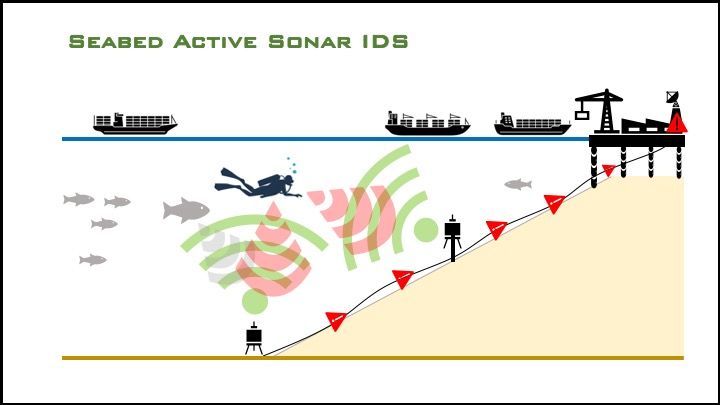
- IDS may also utilize scanning sonar to examine the keels of passing vessels for parasitic attachments such as mines and contraband.
IDS are hard-wired, semi-"closed" systems providing a buffer against passive cyber intrusion. However:
-
IDS are wired to a shore-based junction box and integrated into the larger port C2 network. If not segmented or firewalled, the IDS will be vulnerable to active intrusion via malware residing within the port's IT systems.
-
If the IDS were to utilize wireless communication for C2 or data transmission, from a pierside processing unit or remote communication buoy, for example, the IDS could be vulnerable to both active and passive network intrusion.
-
If a docked vessel utilizes a public WiFi connection and its onboard IDS integrates with onboard C2, the vessel's IDS could be vulnerable to attack from malware residing within the port's IT. Conversely, the port's IT could be vulnerable to intrusion from malware residing within the vessel's IDS or its C2 systems.
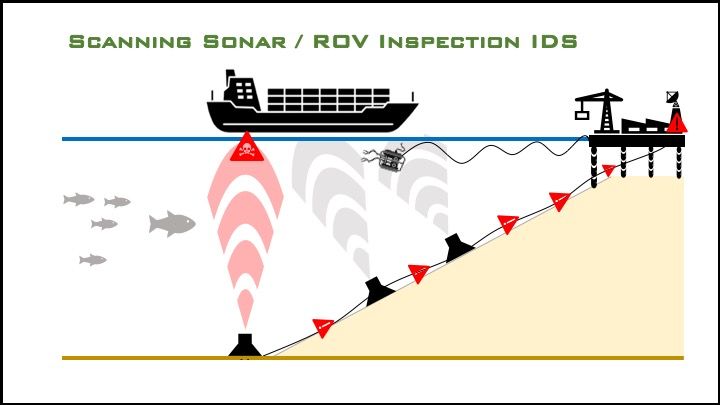
Port underwater security operations may also involve close-in inspection of vessels and port infrastructure (pilings, underwater cables, pipelines) utilizing a remotely operated vehicle (ROV), an unmanned underwater vehicle that is tethered to a C2 unit operating from a pier or manned inspection vessel.

-
While the ROV and C2 unit appear to be closed or "air gapped" (buffered against passive cyberattack), if the unit provides for wireless (WiFi, LTE) connectivity to transmit data, video, or still imagery to a remote location, this system, including the ROV itself, would then be vulnerable to attack. Many COTS ROVs integrate with WiFi-enabled laptop computers or WiFi and Bluetooth-enabled smartphones, using them for C2, video, and data processing.
-
If a wireless-enabled ROV inspection system is integrated into a patrol vessel's C2, the entire port security network, and, by extension, possibly the larger port C2 system, is then vulnerable to attacks originating within the ROV. (The ROV would also be vulnerable to attacks originating within the port's C2).
As underwater communication technologies continue to mature, and as AUVs are integrated into port security operations, IDS may come to rely on acoustic communication for underwater C2.
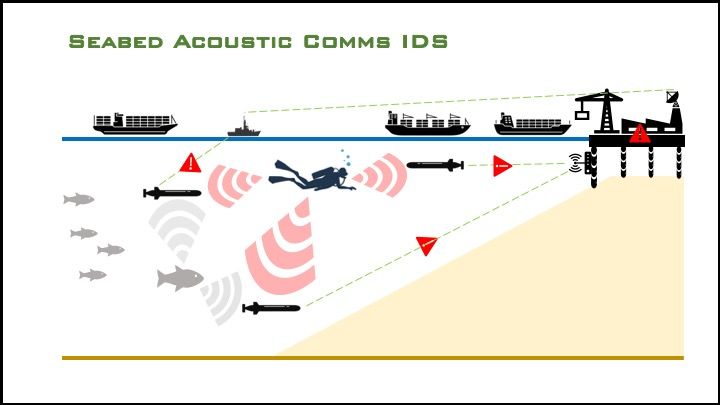
-
The IDS could be vulnerable to a network intrusion via man-in-the-middle attacks wherein adversary (red) underwater network nodes (AUVs, seabed transceivers, hull-mounted or dipped acoustic modems) masquerade as blue nodes using malicious acoustic transmissions.
-
Acoustic communication is possible over long distances, and does not require line of sight, which could enable a malicious node to operate at standoff range, well outside the security perimeter.
UNMANNED SURFACE VEHICLES

USVs are currently undergoing testing and are on track to be widely deployed for port infrastructure inspection and security operations.
-
USVs can be equipped with an array of optical, electromagnetic, and CBRN (Chemical, Biological, Radiological, Nuclear) sensor technologies, and will provide port operators with enhanced, persistent, wide-area surveillance and situational awareness.
-
Using high-resolution multibeam sonar, USVs will replace divers and manned vessels in carrying out complex, dangerous underwater inspection of hulls and port infrastructure.
USVs will integrate with port IT systems and can be controlled and/or accessed via wireless (WiFi, LTE) connectivity. They can therefore be both victims of cyberattacks or exploited as attack vectors.
-
USVs will be vulnerable to attack if they utilize WiFi, Bluetooth, or 4G LTE for remote control or data transmission, all of which have ongoing, well documented security vulnerabilities.
-
In addition to inheriting many of the security vulnerabilities of its predecessor, 5G LTE networks are alleged to contain backdoors accessible to Chinese telecom giant Huawei.
-
An attacker could deauthorize the USV operator and gain control of the vehicle to disable it, compromising security operations and creating a hazard to navigation. The attacker could also direct the USV to physically attack vessels or port infrastructure, or gain access to the larger port security or operational C2 network.
Analysts have speculated that adversary-manufactured consumer/hobbyist UAS (quadcopter drones) could be used in carrying out state-sponsored ISR, or augmented with additional technologies to engage in cyberattacks. This has implications both for adversary-manufactured USVs used in friendly port security operations, as well as general COTS or consumer/hobbyist UMS which could be equipped with specialized intelligence and/or cyber payloads.
-
Chinese consumer/hobbyist UAS manufacturer DJI has come under increased scrutiny by U.S. regulators who have expressed concern that, given the blurry line separating China's state and private commercial interests, DJI's quadcopter drones could be exploited as covert intelligence gathering platforms for Beijing, or even as vectors for cyberattacks.
-
The U.S. Department of the Interior has grounded its drone fleet while it investigates security concerns, and DJI has received an outright ban by the Pentagon. It has also been placed on the "Entity List," the Department of Commerce's Bureau of Industry and Security blacklist.
-
U.S government concerns were bolstered by a 2020 RAND report describing how UAS could be used to carry out cyberattacks against poorly or unsecured wireless networks. "How to Analyze the Cyber Threat From Drones" provides a detailed analysis of how a consumer/hobbyist drone could not only be the victim of cyberattack, but also used as an attack vector in carrying out cyber operations.
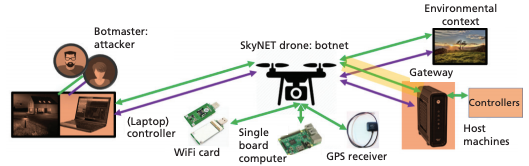
Source: RAND, How to Analyze the Cyber Threat From Drones
While there is no direct evidence of DJI drones being used in state sponsored espionage, if drone-based intelligence operations are in fact a valid security concern, it should also apply to Chinese USVs which will soon be used for a variety of missions, including port security.
-
Zuhai-based OceanAlpha, for example, is one of the largest USV companies in the world. The company designs, manufactures, and markets a range of small USVs for use in offshore monitoring, environmental survey, surveillance & security, and search & rescue.
-
The company operates a 32,000 square meter USV research, development, and testing center at what is now its headquarters at Heung Shan Marine Tech Port.

- OceanAlpha made headlines in 2018 when the company showcased a swarm of 56 USVs.
- The company's USVs are ideal for port security in that they are small, able to carry a range of sensors, and capable of extended, long range operation (in the case of the M75, 15km).
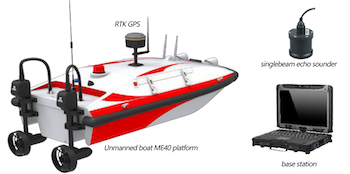
The OceanAlpha ME40 (Hydrographic Survey)

The OceanAlpha M75 (Surveillance & Security)
- Adversary-manufactured UMS used in port security should be of particular concern not only for commercial shippers, but for navies and coast guards operating in ports owned/operated by adversaries who could utilize patrolling USVs as intelligence gathering platforms. For example, the port of Haifa, a commercial port which is also home to the Israeli Navy and a frequent port of call for the U.S. Navy's Sixth Fleet, will be operated by state-owned Shanghai International Port Group beginning this year. China's ownership of, and operational influence over worldwide commercial maritime facilities will only increase as this figures heavily in the Maritime Silk Road Initiative.
CONSUMER/HOBBYIST UMS
▶︎ Unmanned Surface Vehicles (USVs)
If consumer/hobbyist UAS are capable of posing a cyber threat to WiFi networks, so too can WiFi-enabled consumer/hobbyist UMS. And given that consumer/hobbyist UMS are not subject to GPS restrictions (geofencing), they could provide malicious actors with a low-visibility insertion platform to circumvent UAS geofencing and carry out covert cyber or ISR operations within a port's security perimeter.
-
Geofencing refers to the use of a proprietary (i.e. manufacturer deployed and administered) virtual GPS barrier to prevent UAS from straying into airspace surrounding sensitive locations such as military bases, nuclear power plants, and prisons. DJI provides an online mapping tool for its proprietary geofencing system, GEO, that enables users to identify geofenced areas when making flight plans.
-
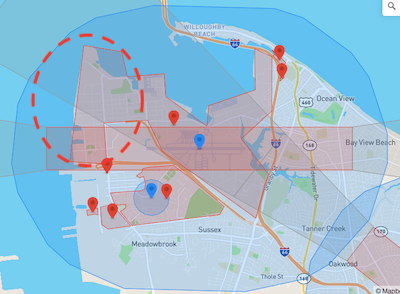
Most sensitive coastal installations have implemented geofencing. Naval Station Norfolk and Naval Base San Diego, for example, are fully geofenced. A red-shaded area indicates a "Restricted Zone," where DJI drones are prevented from flying. A blue-shaded area indicates an "Authorization Zone," which can be "unlocked by authorized users using a DJI verified account."
Source: DJI GEO Zone Map
- U.S. submarine bases are also fully geofenced as demonstrated by Naval Submarine Base Kings Bay and Submarine Base New London.
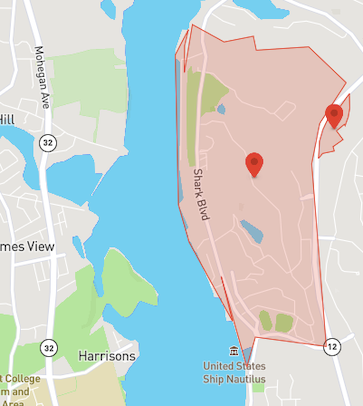
 Source: DJI GEO Zone Map
Source: DJI GEO Zone Map
- Some commercial maritime ports fall under an umbrella of geofencing due to their proximity to airports and other critical infrastructure. For example, the Port of Haifa is partially covered by the fully geofenced Haifa Airport. Note that the overlapping area is not a Restricted Zone, but an Authorization Zone, and while commercial operations are covered, the naval berthing area is fully exposed.
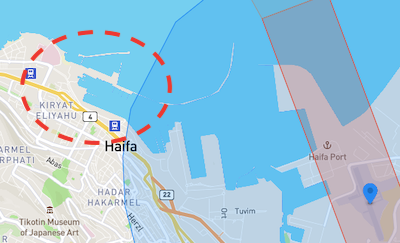
Source: DJI GEO Zone Map
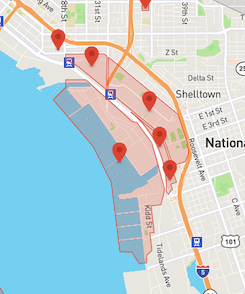
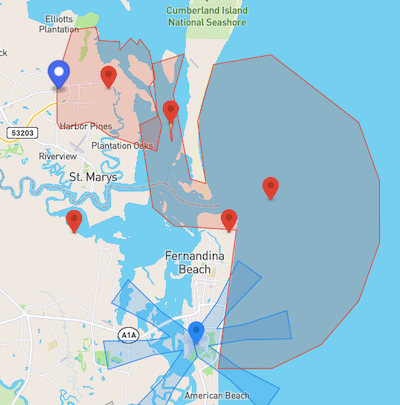
- Geofencing is not consistently applied across maritime facilities. Many large commercial ports enjoy no geofencing at all. The Port of Los Angeles and the Port of Baltimore, for example, even being in close proximity to international airports, have none.
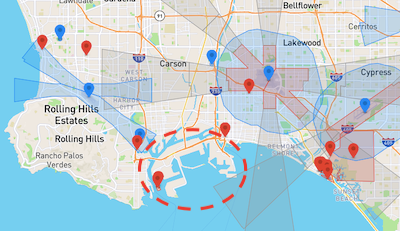
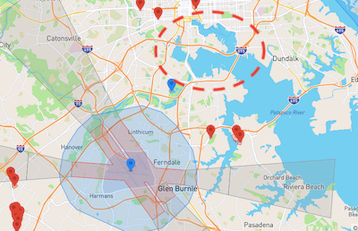
Source: DJI GEO Zone Map
- And here we have the greater Kola Bay region, home to Russia's Northern Fleet and the Main Directorate of Deep Sea Research (GUGI). The only geofencing in sight is that of Murmansk Airport.
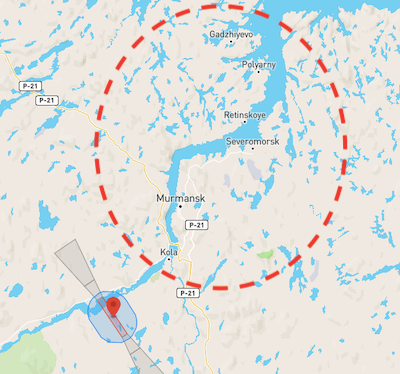
Source: DJI GEO Zone Map
- China's Yulin/Longpo Naval Base is fully (and widely) geofenced. However, Shanghai, China's busiest port, is not.
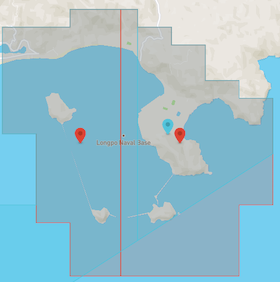
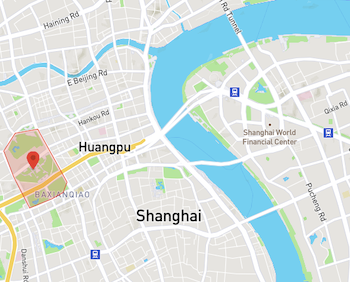
Source: DJI GEO Zone Map
- The absence of geofencing around certain commercial ports and foreign naval installations suggests that local governing authorities do not consider UAS to be a viable security threat (physical or cyber). Such thinking likely extends to the surface domain as well, providing an opportunity for exploitation by consumer/hobbyist USVs.
The availability, affordability, and simplicity of consumer/hobbyist UAS makes them an attractive platform for malicious actors compared to USVs.
-
The market for consumer/hobbyist USVs is currently dwarfed by that of UAS, which is expected to climb from $44 billion in 2018 to $63.6 billion by 2025,
-
USVs are confined to waterways and two dimensions, whereas UAS can (theoretically) be operated anywhere.
-
UAS are highly flexible and offer a wide range of applications and mission sets to a wide range of industries - agriculture, construction, disaster relief, insurance.
However: The ubiquity of the quadcopter makes it easily recognizable, and its domain of operation makes it vulnerable to radar and even visual or auditory detection. Thus, the proliferation of quadcopters, coupled with the use of geofencing in port security, could lead malicious actors to seek out an alternate unmanned platform when carrying out cyber or intelligence operations against sensitive coastal locations.
While many consumer/hobbyist USVs tend to be in the form of remotely controlled toys, many have gained traction as highly capable tools for fishing and marine observation. (NOTE: UMS products cited and pictured below are provided for illustrative purposes only.)
- "Bait boats" are very small, remotely controlled USVs equipped with spring-loaded or trap door bait dispensers, high resolution fish finding sonars, and/or HD underwater video cameras.
-
Bait boats can be operated at ranges of up to 1600 feet (487 meters) - 1/3 of a mile (nearly 1/2 km) - with some capable of GPS and "autonomous" (waypoint navigation) operation.
-
The PowerDolphin from PowerVision is a hobbyist USV capable of autonomous operation via GPS-guided programmable path navigation at a range of up to 1000 meters. The device is equipped with a unique high-def camera that provides imagery both above and below the surface. A fish finding / underwater topography sonar is also available, with a depth capability of 80 meters.

- The Chasing F1 from Maverick Drone Systems is a highly maneuverable fish finding drone that is equipped with a high definition camera, and can be fitted with a trailing bait dispenser or sonar ball. The camera system can operate at a depth of 28 meters and has a range of one meter.

-
Consumer/hobbyist USVs are small (3-5 pounds, less than 2 feet in length) and very quiet, and could be easily disguised as floating flotsam or driftwood to avoid radar or visual detection.
-
Though typical WiFi connections are short range (50 meters or less) a recent Air Force Institute of Technology masters thesis, "[Development of a Drone Mounted Wireless Attack Platform],(https://scholar.afit.edu/cgi/viewcontent.cgi?article=4225&context=etd)" found that, using a directional antenna, a WiFi computer network attack (CNA) could be successful at a range of 3000 meters (nearly two miles). This has implications not only for the air domain, but surface and subsurface as well.
▶︎ Unmanned Underwater Vehicles (UUVs)
UUVs fall into two broad categories: Autonomous Underwater Vehicles (AUVs), which operate untethered and are capable of carrying out preprogrammed missions with little or no intervention, and Remotely Operated Vehicles (ROVs), which are tethered via communications cable to a pier or vessel-based C2 unit and operated by a human pilot.
While state actors or well-equipped/funded nonstate proxies could use sophisticated COTS or indigenously developed AUVs to infiltrate ports, coastal infrastructure, and inland waterways, actors seeking to exploit COTS or consumer/hobbyist underwater vehicles for ISR or cyber operations would be limited by these vehicles' inherent performance limitations and cost.
-
Consumer/hobbyist UUVs are faced with the same technological challenges facing those used in scientific and defense applications: communication, energy, and autonomy. As such, consumer/hobbyist UUVs are exclusively ROVs.
-
The instruments and components necessary for autonomous underwater operation (Doppler Velocity Log (DVL), Inertial Navigation System (INS), obstacle avoidance sonar, acoustic modem, processor, high-density battery) cost several hundred to several thousand dollars apiece (though costs, along with size/weight, are trending lower), with the minimum cost of a single small/micro COTS AUV falling around $10,000.
-
While cost, technological factors, and market demand work against the development of consumer/hobbyist AUVs, it is possible that a malicious actor could construct a homebuilt micro AUV using inexpensive COTS components and use it infiltrate a port, transit to a specific waypoint, adjust its buoyancy to expose an antenna, and engage in ISR or cyber operations. The Amethyst, for example, is a 3D printable AUV frame that could be outfitted with thrusters, a Raspberry Pi, GPS or inertial navigation, and WiFi connectivity.
While technological and financial barriers will likely constrain malicious RC/autonomous unmanned underwater operations for the foreseeable future, tethered operations using consumer/hobbyist or COTS Remotely Operated Vehicles (ROVs) are possible.
-
There are numerous affordable COTS and consumer/hobbyist ROVs that could be used by malicious actors in carrying out acts of surveillance, sabotage, or terrorism. These vehicles are available through retailers such as Amazon.com, or directly from the ROV makers themselves. Prices range from a few hundred to several thousand dollars depending on the underlying capabilities.
-
ROV operational range is limited by the length of the tether. Consumer/hobbyist ROVs generally come equipped with 50-100 feet of tether, however longer spools of 150-300 meters are available with higher-end and professional vehicles. It is also possible to fashion a longer cable by splicing shorter cables together. Professional-grade tethers are neutrally buoyant, meaning the cable would be submerged, and therefore concealed, as the ROV maneuvered beneath the surface.
-
Given their tethered operation, ROVs are not suitable for persistent surveillance or surface cyber operations. However, they could be used for covert underwater reconnaissance of port infrastructure, including pipelines, cables, and seabed IDS sensors. They could also be used in kinetic attacks against port/coastal cyber infrastructure, such as underwater cables or seabed server farms.
POSSIBLE UMS-BASED CYBER ATTACKS
Below are several possible cyberattack methods and scenarios involving UMS as either the victim of the attack, or as the operational attack vector.
▶︎ Zero Day Exploit:
A zero day exploit is a cyberattack that takes advantage of a previously unknown software flaw that enables unauthorized access to a system or larger network. (The flaw has been known for "zero days" when discovered.)
-
A zero day could reside within a port's operational or security IT/OT systems, within UMS C2 software, or within OT utilized by a UMS.
-
A zero day could be exploited at the point of UMS manufacture, with a malware payload propagating to all systems during manufacturing, system maintenance, or upgrade. It could also reside within the software of third party components and instruments used in manufacturing the UMS.
-
Malware could disrupt the UMS C2, inject false data for purposes of deception, drain the vehicle's battery, or use its wireless connectivity to intrude into the port C2 network to disrupt or monitor data and communications traffic.
-
While not explicitly a zero day, a "backdoor" or hard-coded password embedded in the UMS or related OT firmware, if discovered, could be exploited in a similar manner.
▶︎ Man in the Middle Attack
During a man-in-the-middle attack, an attacker impersonates a victim network node in order to intercept transmissions, disrupt network traffic, or inject false data into the stream.
-
An attacker could deploy a consumer/hobbyist USV with an augmented payload (Raspberry Pi and a WiFi card) and use it to generate a rogue WiFi access point. The attacker could then eavesdrop on port network communications, obtain passwords and personal information of network users, or insert malware into crew smartphones or laptops that could migrate to critical port or vessel onboard systems.
-
Similar to the quadcopter scenario outlined by RAND, an augmented USV could be used to penetrate port WiFi networks, potentially gaining access to wirelessly controlled devices critical to port security, such as USVs, or even the wider port security or operational C2 systems.
-
If port security USVs utilize WiFi or LTE for C2 or communications, the attacker could monitor or intercept data or video transmissions, or deauthorize the operator and gain control of the vessels.
▶︎ Position, Navigation, and Timing (PNT) Attack:
A PNT attack involves jamming, disrupting, disabling, or "spoofing" a vehicle's satellite navigation (GPS, GNSS, BeiDou, GLONASS) by either preventing onboard PNT technology from receiving satellite signals (jamming), directly attacking the PNT technology onboard the vehicle, or by manipulating the signals that the vehicle's PNT receivers rely upon (spoofing). PNT attacks are a serious concern for the maritime sector, particularly in certain regions of the world such as the Black Sea and eastern Mediterranean where Russia is believed to engage in GPS jamming and spoofing.
-
A malicious actor could infiltrate a port using a small USV equipped with a GPS jammer and interfere with vessel navigation within the port, significantly disrupting operations.
-
A malicious actor could deploy a small USV equipped with a GPS spoofer to transmit false signals in an effort to gain control of a port security USV. Nearby manned vessels would likely notice the spoof attack, but the USV would not as it lacks the ability to validate position through visual confirmation (though port operators or the vehicle's C2 system may detect navigational deviations and override or employ a kill switch).
-
A malicious actor could exploit a zero-day or mount a man-in-the-middle attack to access the C2 of a port security USV and directly attack its PNT functionality, disabling its receiver or altering its path navigation by inserting or deleting waypoints.
-
An ambitious PNT attack could involve "dragging" the vehicle into nearby vessels or infrastructure, disabling it to create a hazard to navigation, or luring it outside the port to rendezvous with a waiting adversary vessel or shore-based operatives for seizure. In 2011, a U.S. Air Force RQ-170 surveillance drone was captured by Iran when it was allegedly hijacked by a cyber warfare unit operating near Kashmar. The operation is widely understood to have been carried out using GPS spoofing.
▶︎ False Data Injection Attack (FDIA):
An FDIA occurs when a malicious actor alters the data and/or sensor inputs that inform critical decision-making by IT, OT, or human operators.
-
The attack could exploit a zero day to insert a malware payload into an IDS. The zero day could reside within the port's broader security or operational C2 while the IDS is deployed in-situ, or within the IDS manufacturer's IT, with the payload propagating to all deployed IDS during manufacturing, system maintenance, or system upgrades.
-
The payload could execute code that alters fields in IDS databases, blocks sensor inputs, or alters them to generate false targets on the operator's tactical display.
-
The attack could be mounted using acoustic transmissions to "spoof" the IDS into sensing false targets. It could also take the form of an underwater man-in-the-middle attack wherein decoy or malicious communications transmit false data to deceive or overwhelm the IDS.
-
A sophisticated operation might point the IDS interface to a digital twin or decoy network - an environment typically used to identify cyber vulnerabilities or entrap malicious actors, but which, conceivably, could be used to feed ongoing, false (i.e. all clear) sensor inputs to port security C2 systems, enabling underwater intruders to enter the port undetected. A sophisticated state actor could employ this at the onset of armed conflict, clearing the way for divers or mobile mines to effect mission kills before vessels can get underway.
▶︎ AI Intrusion/Manipulation:
Autonomous and artificially intelligent systems require access to large, unstructured datasets for use in algorithmic decision-making or, in the case AI, deep learning. An AI manipulation attack would involve altering or contaminating a dataset, or even replacing an entire AI model, in order to disrupt or degrade a system's decision-making capability or to force outcomes that are favorable to the attacker. Such an attack would be extremely hard to detect, and might even be undetectable. Once discovered, the data would have to be sanitized, and any AI models retrained, while trust would be severely, if not irrevocably, damaged.
-
An adversary could gain access to an IDS and disable or alter its detection algorithms such that they ignore intruder acoustic signatures, or classify them as benign background noise.
-
Alternatively, an adversary could alter the acoustic signature dataset used by the system's detection algorithms or AI to detect, localize, and classify intruders.
▶︎ Acoustic Intelligence:
Port acoustic intelligence would be useful in planning underwater infiltration operations or acoustic cyberattacks. Small hydrophones could be used to gather intelligence on the port's underwater environment, including communications, IDS operations, ambient noise, or the acoustic signatures of vessels, all of which could be used in preparation of the battlespace.
-
An attacker could use a bait boat USV to infiltrate a port and, using the onboard bait dispenser, remotely deploy micro surveillance buoys camouflaged as driftwood or floating debris.
-
The buoys would be constructed using a Raspberry Pi, a WiFi card, and a COTS hydrophone (or perhaps an array of hyrdophones) or acoustic modem. Alternatively, a tethered hydrophone(s) or modem could be deployed via the bait dispenser, or affixed to the keel of the USV.

The Aquarian H2A-XLR Hydrophone

Autonomous Underwater Recorder
- An acoustic modem could be used to emulate false acoustic signatures or decoy communications, penetrate underwater comms networks via an acoustic man-in-the-middle attack, or jam/overload the IDS with ambient noise or loud-hailing.


The Teledyne Benthos Compact Modem
▶︎ Underwater Imagery Reconnaissance:
Underwater imagery would also be important in planning infiltration operations for purposes of ISR, cyberattacks, or kinetic strikes on vessels or port infrastructure.
-
A malicious actor could use a consumer/hobbyist USV equipped with fish finding sonar to penetrate the security perimeter of a major seaport and obtain imagery of the seabed. Some fish finding sonars enable topographic imaging with enough resolution to identify protrusions or man-made objects, while others offer very high definition imaging. Depending on the depth and turbidity of the water, high definition fish finding cameras could also be used.
-
Underwater IMINT could identify the location of IDS sonar heads or hydrophone arrays, security barriers, seabed power and communications cables, and pipelines.
-
COTS and consumer/hobbyist ROVs could be used in underwater reconnaissance, though they would be limited by the length of their tether.
CONCLUSION
Maritime cyberattacks are on the rise, and while port cybersecurity research rightfully emphasizes the vulnerabilities originating within port commercial operations, it should also extend to vulnerabilities originating within, and related to, port physical security operations. Increased automation of port security and the coming integration of UMS and underwater sensor and communication networks will enlarge port attack surfaces and provide malicious actors with an expanding range of exploitable attack vectors. Port UMS will be vulnerable both as targets and as operational attack vectors, and could be used by adversaries operating friendly foreign ports for intelligence gathering or cyber operations. And much as consumer/hobbyist UAS are potential platforms for drone-based ISR and cyberattacks, COTS consumer/hobbyist UMS could be used to infiltrate ports and coastal installations for similar missions. Identifying potential attack vectors and imagining attack scenarios such as those outlined here will help to mitigate the effects of port cyberattacks, and avoid a destabilizing and potentially devastating blow to the global economy.




